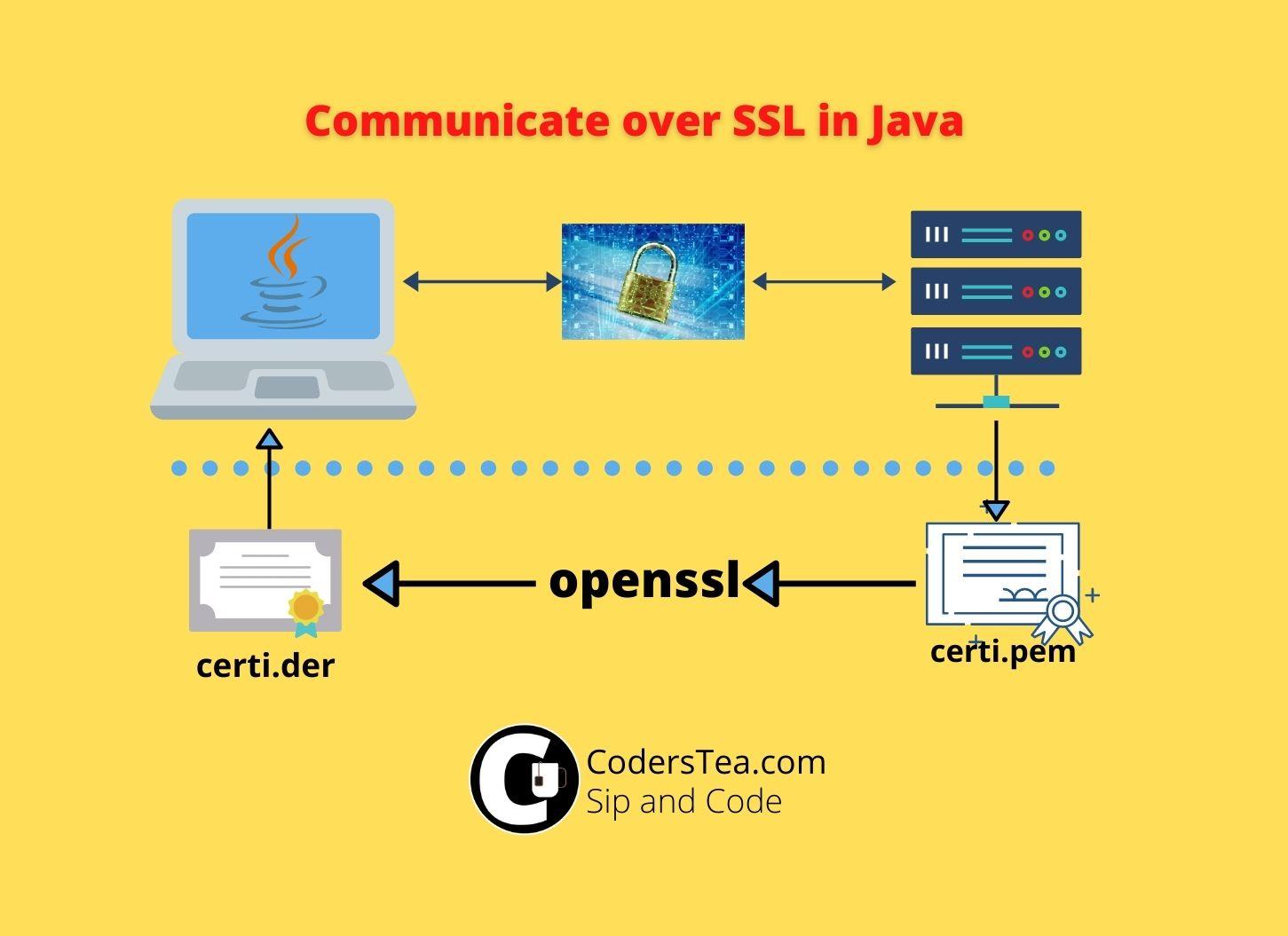
Hey, Tea Lovers! Today we are going to set up the SSL or TLS certificate for securing our communication with another server. If your Java code is trying to connect to DB over SSL\TLS or calling an HTTPS API then you will be needing that server’s root certificate. We will add SSL or TLS Certificate in Java.
To add a certificate via a keytool you have the following options.
- Insert in Java’s Truststore or
- Create your own Truststore if don’t have permission.
Why Insert SSL certificate in Java
When communicating over SSL or TLS Java authenticates the host. If you don’t tell Java that I trust this host then it will throw the following error.
Exception in thread "main" javax.net.ssl.SSLHandshakeException: sun.security.validator.ValidatorException: PKIX path building failed: sun.security.provider.certpath.SunCertPathBuilderException: unable to find valid certification path to requested target
This issue is when Java doesn’t trust the host.
Insert SSL Certificate in Java Keystore
For it to trust it you need to add a host certificate into Java’s Truststore which tells Java that, you trust this host. Let’s look at the steps now.
Get the Host Certificate
First, you have to get the host certificate. You need .cer or .der file. But If you have a .pem file then you have to convert it into .der. Either you can do it online or if you have OpenSSL then you can run the following command.
openssl x509 -in server-certi.pem -inform pem -out server-certi.der -outform der
Add it to Java Truststore cacert
Now that we have got the file, we need to insert it into the truststore. We have to add it to the cacerts of Java.
keytool -import -alias server-name-certi -keystore $JAVA_HOME/jre/lib/security/cacerts -trustcacerts -file /path/to/server-crti.der -storepass changeit -noprompt
changeit is the default password for the truststore. Replace $JAVA_HOME with the java home if you don’t have that value set up already, or you can set it up with the help of this post. -noprompt is for skipping confirmation.
Create your Truststore with keytool
Sometimes you dint have access or permission to the default truststore. In this case, you can create your own and pass it to the Java VM at runtime.
You can do it via code also, but we will stick to the keytool for now. First, run the following command. You will be needing the .der file.
keytool -keystore customstore -import -alias server-name-certi -file /path/to/server-crti.der
It will prompt you for a password, then reconfirm the password, and in the end type yes for confirmation to add the certificate. in case you want to skip the input part then you can use the following. But it doesn’t work on windows.
printf 'Mypassword\nMypassword\nyes\n' | keytool -keystore customstore -import -alias server-name-certi -file /path/to/server-crti.der
After successfully creating the store, it will create a file with the same name as the truststore, customstore in our case, in the same working directly. I will suggest it to create it from where you will be running the java command. you will need to pass it to the Java VM args as the following.
-Djavax.net.ssl.trustStore=customstore -Djavax.net.ssl.trustStorePassword=Mypass
Therefore, while running the java code or jar file it will look like the following.
java -Djavax.net.ssl.trustStore=customstore -Djavax.net.ssl.trustStorePassword=Mypass Hello
Or something like this,
java -Djavax.net.ssl.trustStore=customstore -Djavax.net.ssl.trustStorePassword=Mypass -jar myapplication.jar
If you are running via IDE, then pass it to the run configuration > VM arguments.
Conclusion
We looked at adding the server’s SSL certificate to Java so that it doesn’t throw an SSL Exception. We discussed both the default Java truststore and created a custom one for our use.
In the next post, we will have a look at the DB communication of MySQL and Postgres over SSL and TLS and then how we can add it to Docker to mimic the same.
checkout the other post from CodersTea and all our code at GitHub:
- Mistakes Probably Every Programmer and I Made in the Beginning
- JDBC Connection Pooling Explained with HikariCP
- Stream API: The Hero Without a Cape
See you in the next post. HAKUNA MATATA!!!